Creating Access Keys via the Command Line#
This document guides you through creating Access keys using the AWS command line.
Step 1: Create an IAM user for your AWS account using the EC2 command line.
1aws iam create-user \
2 --user-name MontCacheUser- Step 2: Create the necessary permission policies.
cat >/tmp/CreateCache-Permissions-Policy.json <<EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"cloudwatch:*",
"cloudformation:*",
"eks:*",
"ec2:*",
"ssm:*",
"autoscaling:*",
"elasticloadbalancing:*",
"iam:*Role*",
"iam:*InstanceProfile",
"iam:*InstanceProfiles",
"iam:*OpenID*",
"iam:*Polic*",
"sts:AssumeRole",
"s3:ListBucket",
"s3:GetObject",
"s3:DeleteObject",
"s3:PutObject",
"rds:CreateDBSubnetGroup",
"rds:DescribeDBSubnetGroups",
"rds:CreateDBInstance",
"rds:DescribeDBInstances",
"rds:DeleteDBInstance",
"rds:DeleteDBSubnetGroup",
"rds:DescribeDBEngineVersions",
"rds:DescribeDBSnapshots",
"rds:DeleteDBSnapshot",
"ecr:*"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "iam:CreateServiceLinkedRole",
"Resource": "*",
"Condition": {
"StringEquals": {
"iam:AWSServiceName": [
"autoscaling.amazonaws.com",
"ec2scheduled.amazonaws.com",
"elasticloadbalancing.amazonaws.com",
"spot.amazonaws.com",
"eks.amazonaws.com",
"eks-nodegroup.amazonaws.com"
]
}
}
}
]
}
EOF
policy_arn=$(aws iam create-policy --policy-name CreateMontCache-policy --policy-document file:///tmp/CreateCache-Permissions-Policy.json --output text --query Policy.Arn)
- Step 3: Attach the above permission policies to the IAM user.
aws iam attach-user-policy --user-name MontCacheUser --policy-arn ${policy_arn}
- Step 4: Generate the Access keys for the user.
1aws iam create-access-key \
2 --user-name MontCacheUser
3
4{
5 "AccessKey": {
6 "UserName": "MontCacheUser",
7 "Status": "Active",
8 "CreateDate": "2024-03-09T18:39:23.411Z",
9 "SecretAccessKey": "wJalrXUtnFEMI/K7MDENG/bPxRfiCYzEXAMPLEKEY",
10 "AccessKeyId": "AKIAIOSFODNN7EXAMPLE"
11 }
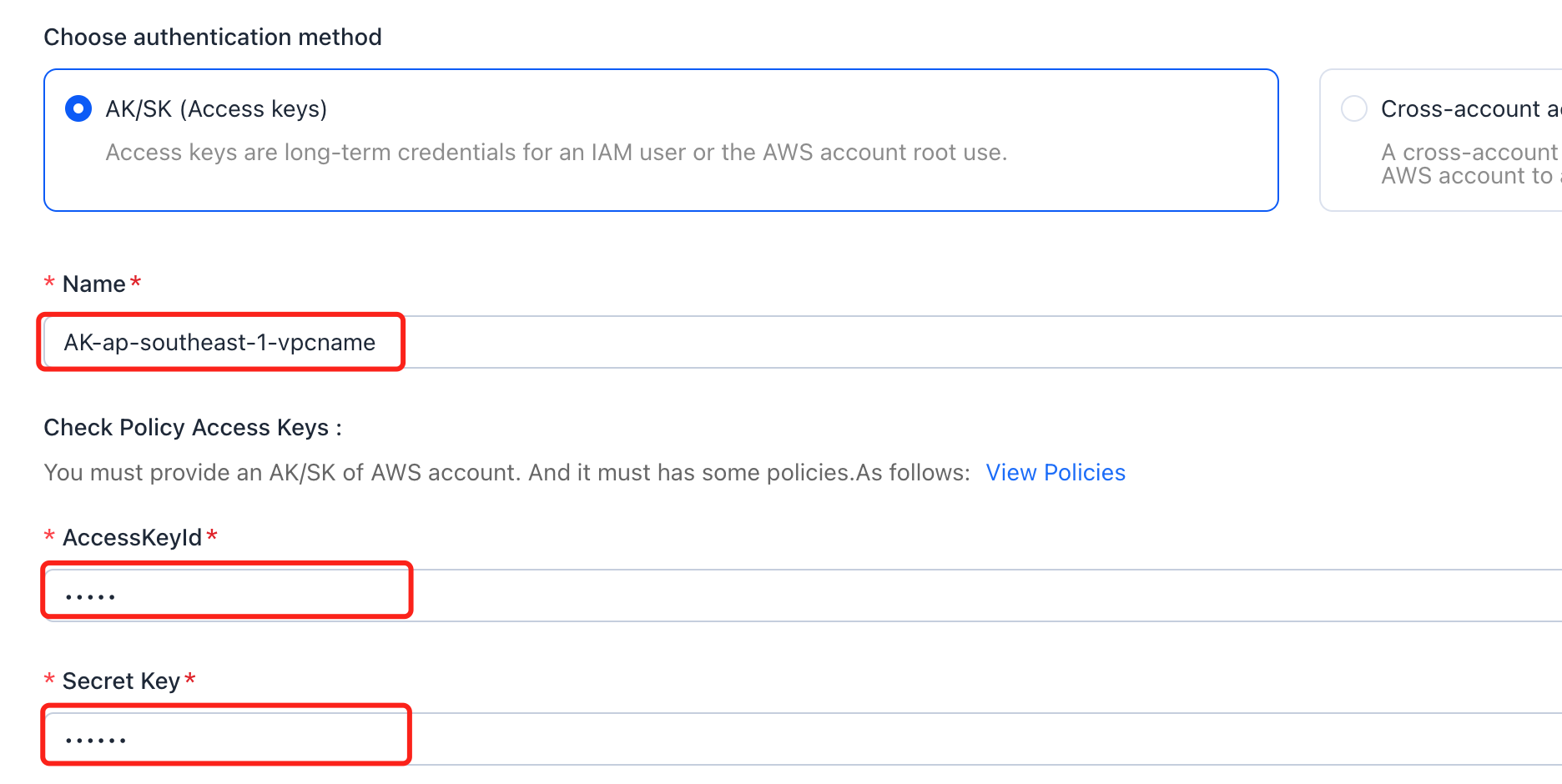
12}Finally, save the generated AccessKeyId and SecretAccessKey in the Montplex Cache.
ON THIS PAGE